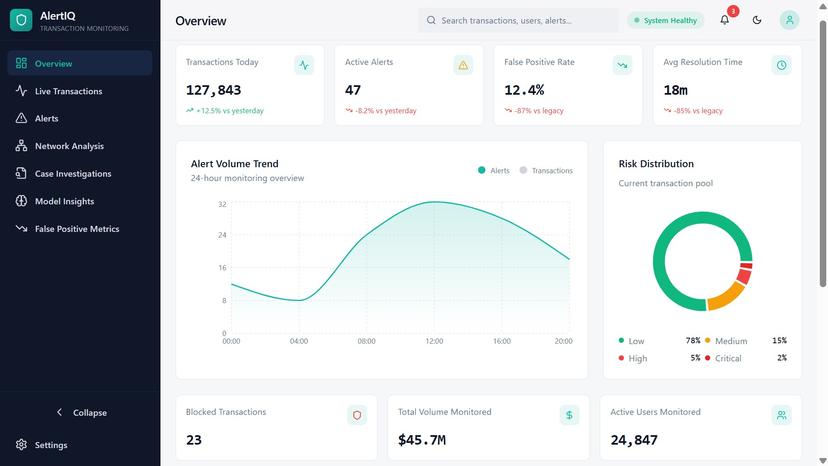
AlertIQ is a next-generation financial crime intelligence platform designed to address the core failures of traditional AML systems. Instead of relying on static rules and fragmented monitoring, AlertIQ continuously analyzes transactions in real time, learning customer behavior, tracking temporal patterns, and mapping complex account networks to uncover hidden risk. The platform fuses behavioral models, time-based intelligence, and relationship graphs into a unified risk engine that detects money laundering, fraud, and compliance breaches before they escalate. Every alert is supported by Model Insights, clearly explaining why it was triggered, what patterns were detected, and how risk evolved over time—ensuring full transparency and auditability. AlertIQ actively measures and reduces false positives using confidence-weighted scoring, analyst feedback loops, and fairness-aware modeling. This minimizes alert fatigue while preserving detection accuracy, allowing compliance teams to focus on genuinely high-risk cases. To streamline regulatory workflows, AlertIQ includes a built-in Compliance Copilot that transforms complex alerts into regulator-ready summaries, supports SAR preparation, and simplifies audits—without removing human oversight. The system is fully aligned with global AML standards, including FATF risk-based principles and regional regulatory frameworks. Built with responsible and sustainable AI, AlertIQ uses lightweight models for detection and applies large language models only for explanations and reporting. The result is an efficient, explainable, and future-ready AML solution that restores trust, reduces operational risk, and transforms how institutions fight financial crime.
7 Feb 2026

As cyberattacks rise, SOC teams face alert fatigue and slow manual triage. Our AI-powered Tier-0 SOC Analyst workflow, built on Opus, automates intake, analysis, risk scoring, and reporting to cut false positives and improve efficiency. We built a simple UI where analysts can upload emails, syslogs, SIEM logs, file metadata, text, and URLs in formats like TXT, PDF, CSV, or direct links. The UI securely sends all inputs to Opus via API, ensuring wide coverage and strong integration. Opus extracts raw content and normalises everything into a unified JSON structure with reliable validation and retry logic. Large-scale IoC extraction identifies IPs, domains, URLs, hashes, and email IDs. Since external services were unreliable, we built a RAG module to classify suspicious or malicious patterns. All IoCs then go through an enrichment stage that adds context, reputation, threat tags, domain age, and confidence, producing a consistent enriched dataset. Two decision nodes handle triage: the first checks whether an IoC is malicious. Clean IoCs go straight to output for automatic report generation, while malicious ones are severity-scored and reviewed by AI. The second node checks if the severity is equal to or greater than 70. Lower scores generate tickets automatically; higher scores trigger human review before finalisation. AI review occurs at key stages—normalised data, enriched IoCs, severity, and final ticket—while human review is reserved for high-risk cases. The workflow ends by generating a report and audit trail, displayed on the UI for full visibility. The system aligns with the UAE and GCC visions in the Middle East by demonstrating a secure, efficient, and scalable AI-driven cybersecurity model. Note: Add our RAG PDF to the RAG Extraction input: https://drive.google.com/file/d/1HYgv4h4W0oWzx2wcMFyGerX1e-4Ba-X5/view Also generate your own PDF API key and add it to the Bearer Auth field in the Report and Audit Artefact Generation node.
19 Nov 2025